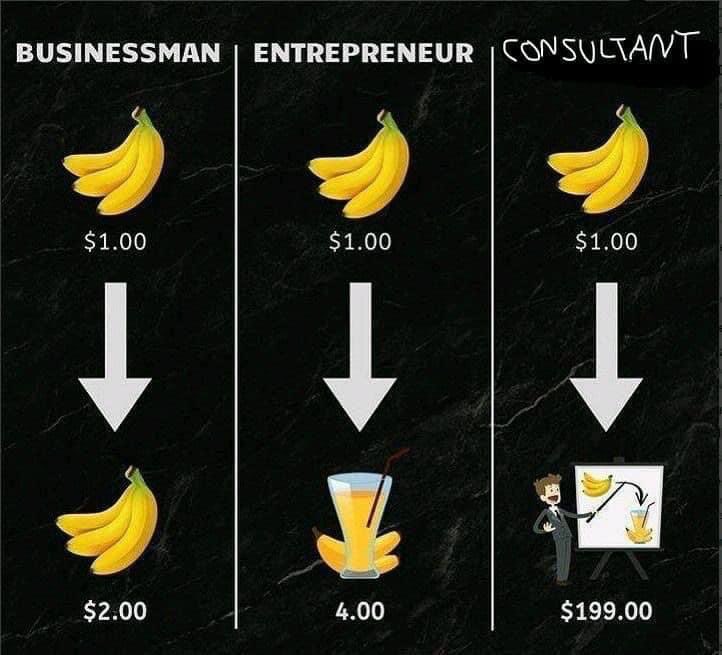
Source: “Internet”. Apologies, this flew along some timeline. If you made this, please let me know in the comment and I will give proper credit!
It’s true, though. Consultants managed to ruin their reputation in the past 2 decades. Once, Business Consultant meant seasoned, experienced business leaders. Nowadays, it’s too often junior university graduates, that senior management uses as an excuse to drive an agenda through political cliffs.
Having been on both sides of this table, it feels just too natural or even tempting not to cash out on management needs to make an argument.