
Yep, he’s right. We’re half way done. I think, this year that’s indeed good news.

Yep, he’s right. We’re half way done. I think, this year that’s indeed good news.
Aber nur solange die Künstliche Intelligenz nicht weiterentwickelt wird. 🤷🏻♂️

Andrew Yang wants people to get paid for the data they create on big tech platforms like Facebook and Google, and with the Data Dividend Project launching on Monday, he believes he can make it happen.
Andrew Yang used to be the Presidential Ambassador for Global Entrepreneurship, appointed by Barack Obama in 2015. He works as an lawyer, and entrepreneur, and often appears as political commentator.
The program revolves around Californian regulation, that apparently recognizes “Data as a property”, making information originating from an individual it’s ownership. (IANAL, though…). Both The Verge and the webpage refer specifically to the California Consumer Privacy Act (CCPA) and the Data Dividend’s task to establish likewise regulation across the country.

Data Dividend Project, My Data, My Money.
It’s like Universal Basic Income, but with your Data.
While the idea appears to be appealing and brings a new spin to the debate of Big Tech and Big Data, signing up with not only one but many emails gives the approach some taste 😉
Big Tech is indeed earning Big Money and for the consumer there often nothing left but being the product. The situation led to numerous discussions in the European Union before, that is much more sensitive to data and privacy for historical reasons. While GDPR addresses lot’s of concerns, data ownership and charging for usage is an entirely different concept, that, to my knowledge, has never been demanded with this emphasis before. Paying the user for allowing Big Tech to run their business models would change the entire game. Fundamentally.
During this years wwdc2020, Apple announced it’s own silicon for future Mac computers. This is HUGE. After the switch from 68xxx to PowerPC and to Intel, this is the fourth change of HW Platform for the company. Mainly, it means a huge message to Intel, who has been providing CPUs for the popular Mac Computers.
Schon gestern konnte man die App wohl herunterladen, aber mit Pressekonferenz angekündigt ist sie erst heute um 10.30 worden. Die App ermöglicht es, künftige Ausbrüche des Virus leichter nachzuvollziehen. Das funktioniert natürlich nur, wenn mehr Leute an der Datenerhebung teilnehmen. Die Architektur der App und der Infrastruktur erlauben es nicht, Bewegungsprofile der Benutzer zu erstellen.
Jetzt die Corona-Warn-App herunterladen und Corona gemeinsam bekämpfen.
Source: Bundesregierung | Unterstützt uns im Kampf gegen Corona.
Der Chaos Computer Club (CCC) vergibt keine Siegel oder Certifikate für die Güte von Software. Aber das Lob des Vereins für den Verantwortungsvollen Umgang der App mit der Ihr anvertrauten Informationen kommt dem sehr Nahe.
The rumours ain’t new, but appear to become more tangible. This time Ars Technica reports an announcement could happen as early as this years WWDC.
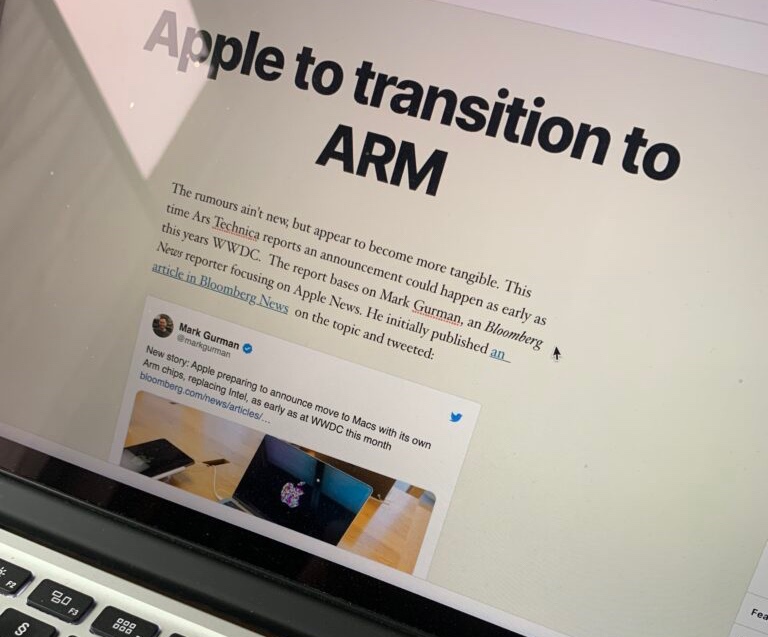
The report bases on Mark Gurman, an Bloomberg News reporter focusing on Apple News. He initially published an article in Bloomberg News on the topic and tweeted:
Not only cost structure and ownership of IP is a significant driver for Apple’s motivation to transition. Most likely, the move will also mean good/bad news for customers and Intel:
Report claims internal Apple testing has seen “sizable improvements” over Intel.
From the article
Source: Ars Technica

The market for collaboration tool has been sparked by Slack a few years ago. It has been subject to heavy fights since. Microsoft Teams not only entered the market but overtook the early mover quickly. The fight escalated perceivably when Slack accused Microsoft of ripping off its ads in late 2019.
AWS and Slack recently announced a partnership, indicating how hot the market apparently still is. With these two heavyweights in the ring, expect some movement in the space.
Source: The Verge
Hacker hacken… Türkische Moscheen und deren Minarette, um auf den Lautsprechern der Einrichtungen “Bella Ciao” anstelle der üblichen Gebete zu spielen.
Dem Nachrichtensender N-TV zu Folge ein Angriff von türkischen Hackern.
Since COVID-19 let’s us work from home, we all made our experiences with Videoconferences. The tools make it possible to work from home, yet some still have to get used to the new freedom. We all know the feeling in these conferences, with colleagues listening or not, playing with their pets, kids or Zoom Backgrounds. Toggl, maker of fantastic time tracking software, nails it:
