Only days after Clearview hit the news, The Economist runs an article on how the Combating Terrorism Technical Support Office (CTTSO), an agency of the US defence department, has developed another dystopian tool to identify people by their heartbeat.
Category: Security & Privacy
-
The Y2038 Problem
The Y2038 problem is similar to the Y2K problem. We’re exactly in between both about now. Both are 18 years away, in either direction. While Y2K is over and was obvious to everyone, Y2038 is not.
The issue here relates to a representation of date and time in Unix systems, and is therefore sometimes referred to as Unix Y2K. The root is the convention to store date and time information as 32bit unsigned integer in such systems. This means, possible values are limited. Time-differences in seconds, starting from 01.Jan 1970 cannot span beyond 03:14:07 UTC on 19 January 2038.

Calendar The Y2038 problem will make all calculations beyond this date impossible, until migrated to another representation. At the time being, this seems far away. However, the problem casts its shadows already. Industries, in particular financial markets, often rely on long term forecasts.
Governance issued treasury bonds come with with the longest maturity. Often twenty years, sometimes thirty years. Calculations for complex, long running financing models easily try to estimate returns 20 years and beyond into the future. This is already beyond the problematic date that Y2038 brings. The code to run these calculations is typically complex and stable. Sometimes, it is as old as from 1970. Back then, this date-representation Unix engineers introduced this approach. 32bit covered a long period. John Femellia has a thread, over at Twitter, telling a story about the upcoming issues today.
-
This week in dystopia.
This week in dystopia: The New York Times has an article about the next steps in dystopian future. A start-up evolving face recognition algorithms, fed by a database with facial images, scraped from the open web.

Clearview – This week in Dystopia. A little-known start-up helps law enforcement match photos of unknown people to their online images — and “might lead to a dystopian future or something,” a backer says.
The New York Times: The Secretive Company That Might End Privacy as We Know ItFurther, the article describes the sheer size of the database. At a rate of massive duplicate numbers, three billion images is still impressive.
The system — whose backbone is a database of more than three billion images that Clearview claims to have scraped from Facebook, YouTube, Venmo and millions of other websites — goes far beyond anything ever constructed by the United States government or Silicon Valley giants.
The New York Times: The Secretive Company That Might End Privacy as We Know ItIn times in which criticism of big tech is on the rise. Just this week Jannis Brühl, Head of Tech News Department at @sueddeutsche Zeitung published an opinion that this technology is dangerous and should be banned,. The article include an appeal to German government to create legislation to do so. Jannis is in good company with other tech critics like Eyvgen Morozov
Source: The Secretive Company That Might End Privacy as We Know It
-
Microsofts Patch Tuesday
Y’all install Microsoft Patch Tuesday patches within 24h, right? This time Krebs On Security has some rumours that make you want to really install these patches in time.
Update: Washington Post reports, the NSA warned Microsoft about it.
-
SHA-1 is a Shambles
SHA-1 is a Shambles: Hashing Algorithm SHA-1 has seen collision attacks before. Gaëtan Leurent and Thomas Peyrin Published a chosen-prefix collision for SHA-1.
Source: SHA-1 is a Shambles
-
Security Nightmares beim 36C3
Security Nightmares – Frank und Ron beim 36C3 in Leipzig Wie jedes Jahr , jedenfalls seit 1999 während des 19C3 in Berlin, haben Frank und Ron auch dieses Jahr wieder Ihren Vortrag Security Nightmares beim 36C3 zu Sicherheitsbezogenen Vor- und Rückschauen gehalten.
In einer Rückschau auf diesen ersten Vortrag “vor zwanzig Jahren” blicken die beiden auf die Vorhersagen von Damals und die Ereignisse der letzte Jahre zurück und fassen den ganzen Zeitraum der beiden Jahrzehnte damit zusammen, ob man Makros erlauben möchte. Makros waren schon 1999 (Melissa, I love you) wie heute (Emotet) einer der wichtigsten Angriffsvektoren für Malware. Der folgende Rückblick auf die letzten zehn Jahre alleine fällt etwas technischer aus. Trotzdem ruft der Teil einige schöne Ereignisse noch einmal ins Gedächtnis. Darunter z.B. den Aufschrei Deutschlands gegen Streetview, die Debatte um intelligente Stromzähler oder die elektronische Gesundheitskarte. Themen, die auch bis heute nicht vollkommen abgeschlossen sind.
Ein “Internet-Normalitätsupdate” setzt jüngere und auch noch laufende Angriffe mit bekannten Zahlen in Perspektive.
Darüber hinaus setzt der Vortrag sich mit Rückschauen in den Themenfeldern E-Gov, Datenreichtum und Crypto (SPD Mitgliederbefragung!), Geschäftsfelder, Crypto, Sport und Bemerkenswertem auseinander, bevor sich Frank und Ron den Stichworten für 2020 widmen. Wenig technisch wagen die beiden eine Prognose zu Berufsfeldern, die die Cyber-Situation hervorbringen könnte. Das reicht von der Cyber-Nachsorge für das Seelenheil Betroffener, über die Cyberfantasy-Geschichtenschamanen, die magiehafte Technologie nachvollziehbar erzählen können, bis zu Verzerrungs-Sucher und IPv6 Exorzisten
Wie jedes Jahr ein interessanter und unterhaltsamer Vortrag. Auch wenn ich die Lesung nicht selbst hören habe können, lohnt sich die Aufzeichnung auf media.ccc.de nachzusehen.
-
(ISC)2 mailed me
Dear Andreas,
You have satisfied your Annual Maintenance Fee (AMF) and Continuing Professional Education (CPE) requirements for your CCSP.
Your CCSP certification has been renewed to a new three-year cycle!Happy to be certified again!
-
Netflix (Security) on Youtube
Netflix (Security) on Youtube: Netflix Security runs a YouTube Channel! As opposed to the company channel, it does not only broadcast previews! This is a great subscription for security practiconers!
Via Stephanie Olsen (on LinkedIn).
-
Nicht witzig.
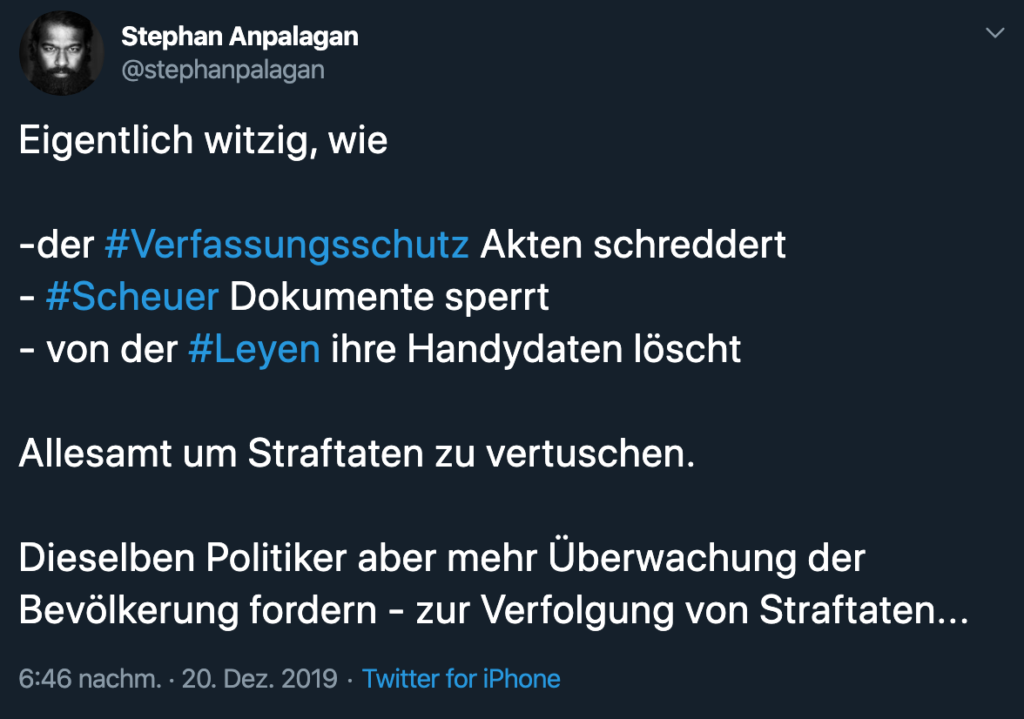
@stephanpalagan on Twitter Stephan Anpalagan@stephanpalagan hat da schon recht irgendwie. Blos finde ich das eigentlich gar nicht so witzig…

